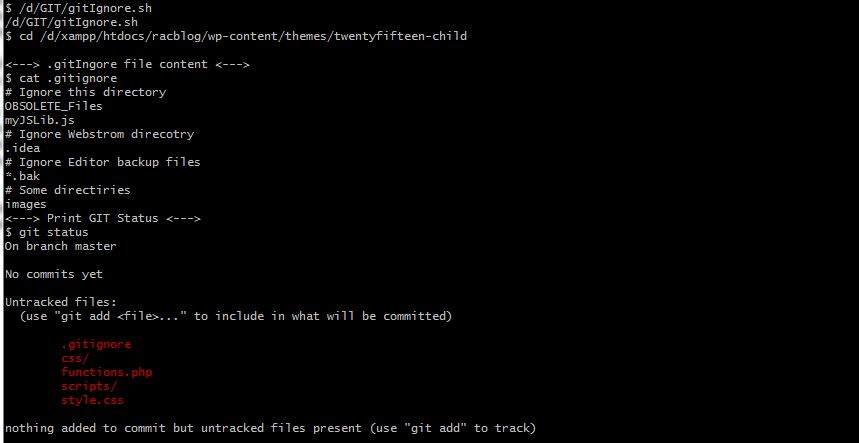
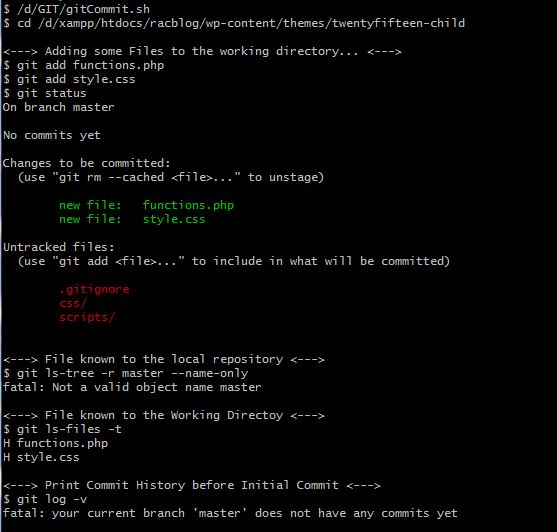
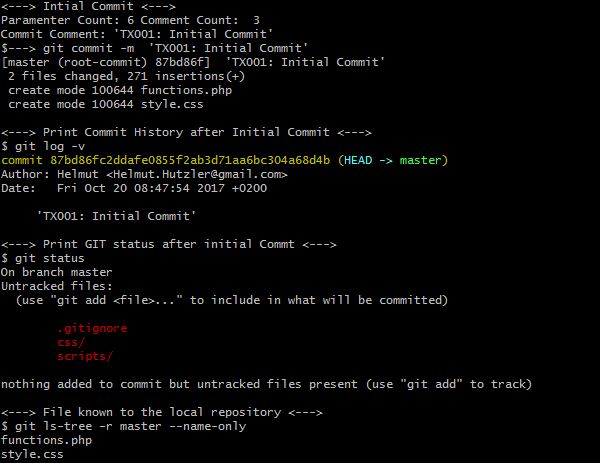
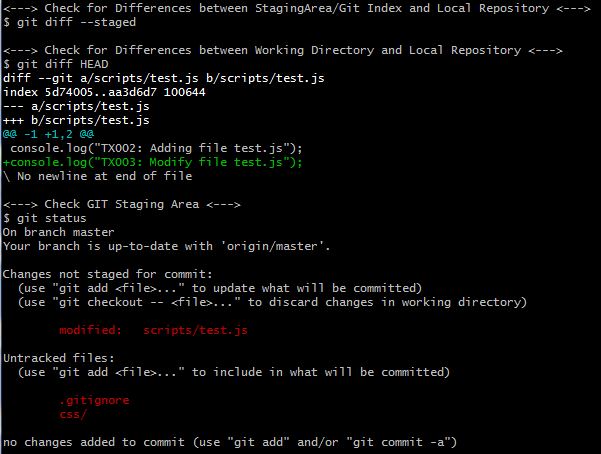
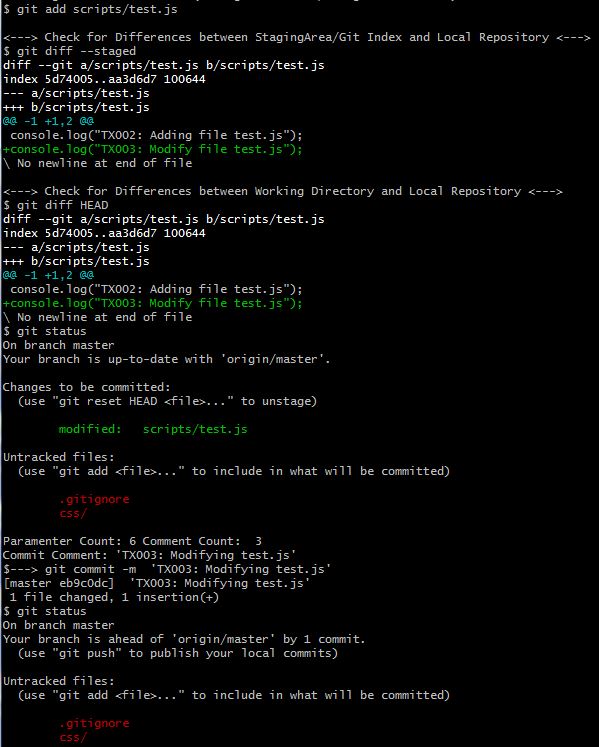
×
![]()
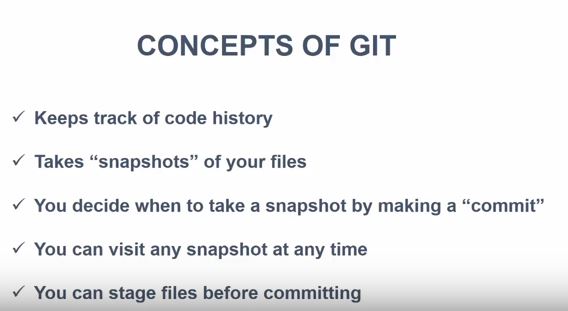
Tools Used for this Tutorial
| Tool |
Tool Version |
| Curl |
7.56.1 (x86_64-pc-win32) libcurl/7.56.1 OpenSSL/1.1.0g (WinSSL) |
| Google Chrome |
Version 61.0.3163.100 (Official Build) |
| Google Dev Tools |
Version 61.0.3163.100 (Official Build) |
| bash shell |
4.4.12(3)-release |
Overview – Login to a WebSite in 3 Steps
| Script Name |
Action |
Return |
| WRlogin.sh |
Login to WebSite using Username Password |
JSESSIONID cookie |
| WRlogin2.sh |
Redirect Request after sucessfull Login |
X-CSRF-TOKEN via HTML Meta Tags |
| WRData.sh |
Access the login protected WebSite |
Inverter Data like: Current Power, .. |
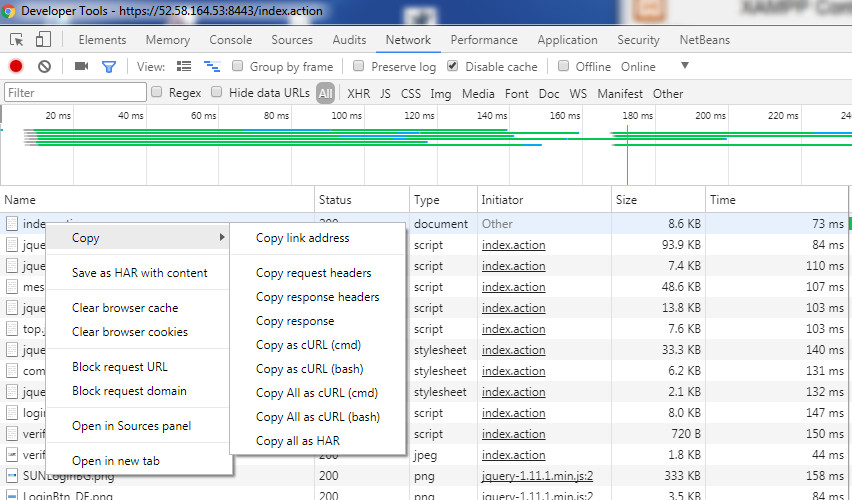
Curl Usage with Google Dev Tools – First steps
To copy Curl Syntax for bash Shell do the following
- Load your inital WebSite a first time
- Press F12 to attach/open Google Dev Tools
- Reload your Page
- Navigate to Network Tab
- Right click the desired API call
- Select “Copy” -> “Copy as cURL (bash)”
| Retrieve the cURL bash Command using Google Dev Tools |
 |
Run our first cURL command
- Paste the cURL command to a bash Shell
- Add -v switch to get HTTP header dumped
- redirect stderr by adding: 2>&1
$ curl 'https://52.58.164.53:8443/index.action' -H 'Pragma: no-cache' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.8' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.100 Safari/537.36' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8' -H 'Cache-Control: no-cache' -H 'Cookie: JSESSIONID=1jzw19tuvg42wl93fxp1exzkf' -H 'Connection: keep-alive' --compressed --insecure -v 2>&1
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
...
{ [5 bytes data]
< HTTP/1.1 200 OK
< Expires: Thu, 01-Jan-1970 00:00:00 GMT
< Set-Cookie: JSESSIONID=ioyf0enlkduy1geo82r2tryk8;Path=/;Secure;HttpOnly
< Cache-Control: no-store,no-cache
< X-Frame-Options: SAMEORIGIN
< X-Download-Options: noopen
< X-XSS-Protection: 1;mode=block
< Strict-Transport-Security: max-age=31536000;includeSubdomains
< X-Content-Type-Options: nosniff
< Content-Language: de-DE
< Content-Type: text/html; charset=utf-8
< Content-Length: 8471
...
HTTP Status of our first cURL request
- The Website gets loaded sucessfuly -> HTTP/1.1 200 OK
- The Website Content-Length is: 8471
- The Website uses cookies: JSESSIONID
- The Website uses https protocol
Use the Google Dev to understand the Login Logic
| JavaScript and JavaScript Files load by the Initial Request |
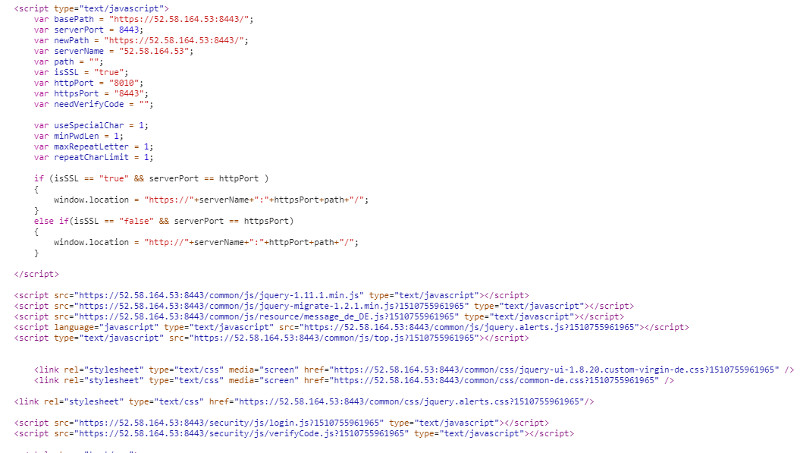 |
index.action loads 2 javascript files
Processing and Validation of Login Form
var verifyResult;
$("#login").click(function() {
if (!allowLogin) {
jAlert(browserMessage, Message.alarm_info, '{"' + Message.sur + '":"OK"}');
clearPassword();
return;
}
var userName = $.trim($("#userName").val());
var password = $("#password").val();
if (!loginValidate(userName, password)) {
clearPassword();
return;
}
var showVerifyCode = document.getElementById("verifyCode_tr").style.display;
comitLogin(userName, password);
});
- For our cURL tutorials we can skip this Step as we already know username / password
- Let’s review the JS function comitLogin()
Login Code implemented via sync. AJAX POST resquest
function comitLogin(userName, password) {
if ($("#veryCode").is(":visible")) {
if (!validateVCodeLength()) {
clearPassword();
return;
}
}
var code = $("#veryCode").attr("value");
$.ajax({
url : basePath + "security!login.action",
type : "POST",
async : false,
dataType : "json",
data : {
"userName" : userName,
"password" : password,
dateTime : new Date().getTime(),
"veryCode" : code
},
cache : false,
beforeSend:function (XMLHttpRequest)
{
//let go
},
success : function(res) {
clearPassword();
$("#pass1").val("");
$("#pass2").val("");
$("#loginErrorMsg").html("")
$("#loginErrorMsg2").html("");
if (res.retMsg == "op.successfully") {
window.location.href = newPath + "securitys!tologin.action";
return;
} else if (res.retMsg == "op.update") {
$("#loginView").hide();
....
- For sending username,password,date and verificationCode a POST request is used
- The remote function to be called is security!login.action
- A successfull login should return: “op.successfully”
- After successfull login a page redirection is triggered to: securitys!tologin.action
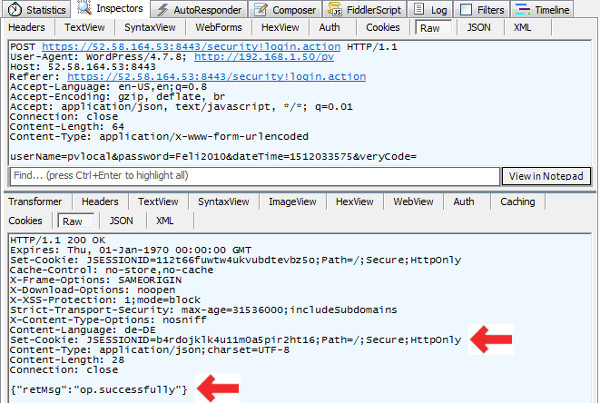
Step 1: Implement the Website JavaScript Login with bash/cURL
| Set breakpoint in AJAX POTS when returning from AJAX POST request |
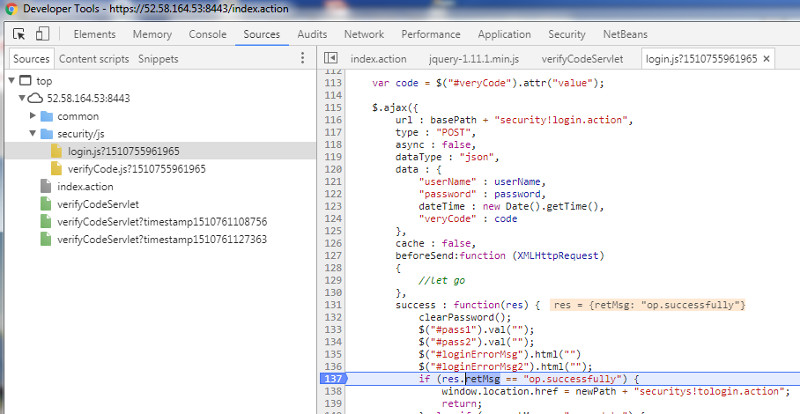 |
| Login the Page – Login process is paused |
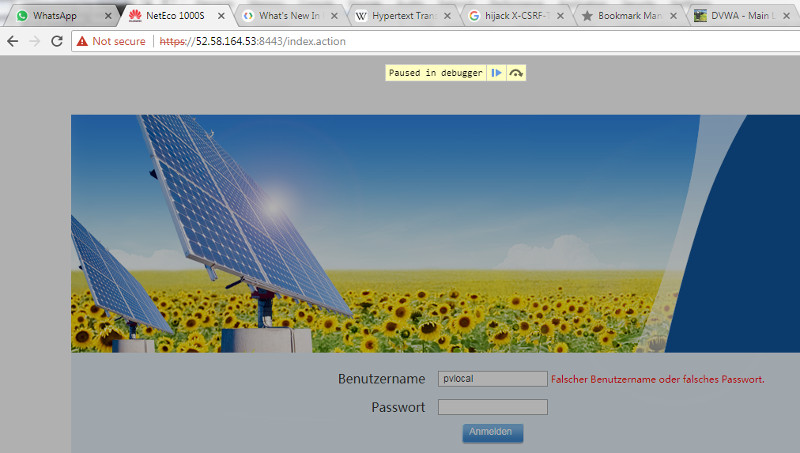 |
| Verify Response and Request Headers |
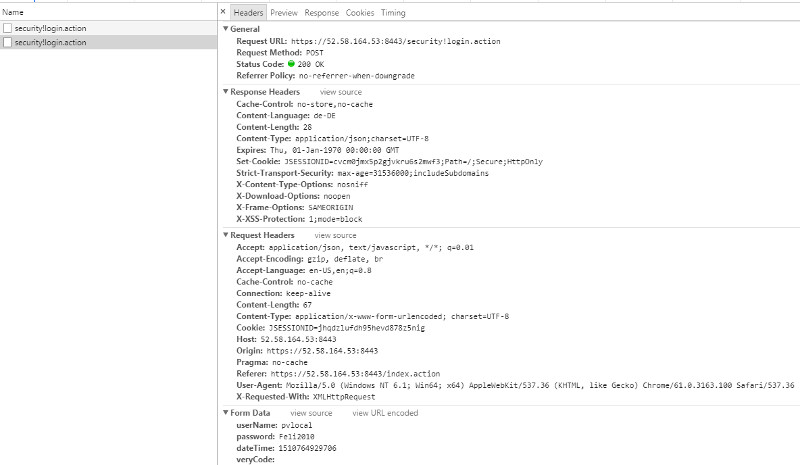 |
- For further processing we need to use the JSESSIONID returned by the Response header
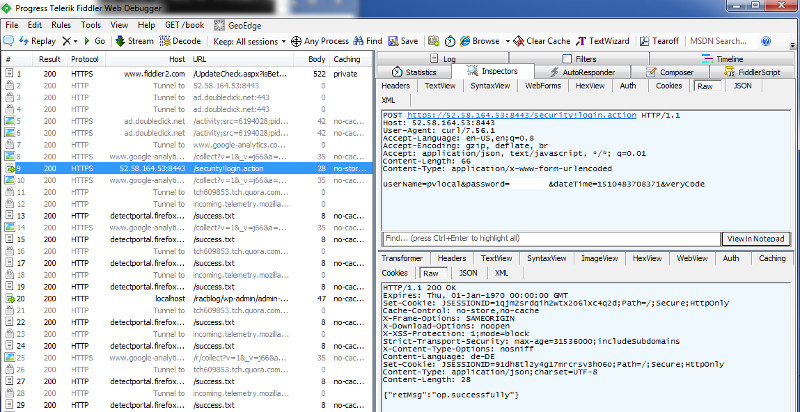
Paste above Output to a Bash Shell
$ curl 'https://52.58.164.53:8443/security!login.action' -H 'Pragma: no-cache' -H 'Origin: https://52.58.164.53:8443' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.8' -H 'User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.100 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded; charset=UTF-8' -H 'Accept: application/json, text/javascript, */*; q=0.01' -H 'Cache-Control: no-cache' -H 'X-Requested-With: XMLHttpRequest' -H 'Cookie: JSESSIONID=jhqdzlufdh95hevd878z5nig' -H 'Connection: keep-alive' -H 'Referer: https://52.58.164.53:8443/index.action' --data 'userName=pvlocal&password=PPPP&dateTime=1510764929706&veryCode=' --compressed
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
curl: (60) SSL certificate problem: self signed certificate in certificate chain
More details here: https://curl.haxx.se/docs/sslcerts.html
curl failed to verify the legitimacy of the server and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.
-> Disable SSL verification by using -k switch
$ curl 'https://52.58.164.53:8443/security!login.action' -H 'Pragma: no-cache' -H 'Origin: https://52.58.164.53:8443' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.8' -H 'User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.100 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded; charset=UTF-8' -H 'Accept: application/json, text/javascript, */*; q=0.01' -H 'Cache-Control: no-cache' -H 'X-Requested-With: XMLHttpRequest' -H 'Cookie: JSESSIONID=jhqdzlufdh95hevd878z5nig' -H 'Connection: keep-alive' -H 'Referer: https://52.58.164.53:8443/index.action' --data 'userName=pvlocal&password=PPPP&dateTime=1510764929706&veryCode=' --compressed -k -i
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 95 100 28 100 67 28 67 0:00:01 --:--:-- 0:00:01 196HTTP/1.1 200 OK
Expires: Thu, 01-Jan-1970 00:00:00 GMT
Set-Cookie: JSESSIONID=1pt4jamjah1vbl44uep5ecvzm;Path=/;Secure;HttpOnly
Cache-Control: no-store,no-cache
X-Frame-Options: SAMEORIGIN
X-Download-Options: noopen
X-XSS-Protection: 1;mode=block
Strict-Transport-Security: max-age=31536000;includeSubdomains
X-Content-Type-Options: nosniff
Content-Language: de-DE
Set-Cookie: JSESSIONID=a5sjmaztpwa81acg06hymnxgb;Path=/;Secure;HttpOnly
Content-Type: application/json;charset=UTF-8
Content-Length: 28
{"retMsg":"op.successfully"}
-> cURL Request works Now
Testing an Invalid Login by changing password to xxxx
$ curl 'https://52.58.164.53:8443/security!login.action' -H 'Pragma: no-cache' -H 'Origin: https://52.58.164.53:8443' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.8' -H 'User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/61.0.3163.100 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded; charset=UTF-8' -H 'Accept: application/json, text/javascript, */*; q=0.01' -H 'Cache-Control: no-cache' -H 'X-Requested-With: XMLHttpRequest' -H 'Cookie: JSESSIONID=jhqdzlufdh95hevd878z5nig' -H 'Connection: keep-alive' -H 'Referer: https://52.58.164.53:8443/index.action' --data 'userName=pvlocal&password=xxxx&dateTime=1510764929706&veryCode=' --compressed -k
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 125 100 58 100 67 58 67 0:00:01 --:--:-- 0:00:01 348 {"retMsg":"Falscher Benutzername oder falsches Passwort."}
Create a Bash Script for Automation – WRlogin.sh
#!/bin/bash
#
# Use Google Dev dev tools and select Copy as cURL (bash) to learn quickly about the Curl Syntax for a HTTP request
#
# After a successfull login a NEW JSESSIONID returned from the response cookie should be used for subsequent requests
#
loginCredentials="userName=pvlocal&password=Feli2010&dateTime=1510483708371&veryCode"
url="https://52.58.164.53:8443/security!login.action"
echo "--------------------------------------------------------------------------------------------------------"
echo "-> URL :" $url
echo "-> INPUT Cookie :" $cookie
echo "-> INPUT Login Credentials :" $loginCredentials
echo "-> OUTPUT :" NEW JSESSIONID cookie after successfull Login
echo "--------------------------------------------------------------------------------------------------------"
#
# DebugON set, possibly to the empty string will printout add. trace info
# To enable Debugging run: $ export DebugON
#
if [ $DebugON ]; then
echo "DebugON is set, possibly to the empty string"
set -x
fi
#
# Only use the needed HTTP header Fields - Most Http Header Fields copied from our Google DEV Tool cURL copy we do not need
curl_header1='Accept-Language: en-US,en;q=0.8'
curl_header2='Accept-Encoding: gzip, deflate, br'
curl_header3='Accept: application/json, text/javascript, */*; q=0.01'
#
# Arrays makes this much easier. Don't use Quotes here as $cookie and $csrf_token content uses spaces !
#
args=("-k" "-v" "$url" -H "$cookie" "--data" "$loginCredentials" -H "$csrf_token" -H "$curl_header1" -H "${curl_header2}" -H "${curl_header3}")
#
echo "---------------------------------- cURL command to be executed -----------------------------------------"
echo curl "${args[@]}"
echo "--------------------------------------------------------------------------------------------------------"
output=$( curl "${args[@]}" 2>&1 )
#
# Sucessfull Login returns following string
# '"retMsg":"op.successfully"}
#
login_status=""
login_status=$(echo "$output" | grep retMsg | awk -v FS="(retMsg\":\"|\"})" '{print $2 }')
#
# Note; login.sh return two occurances of string:
# Set-Cookie: JSESSIONID=h0eaof37hnta1wtjlk1j1nig2;Path=/;Secure;HttpOnly
# As we are only intrested on the 2.nd one use: sed -n 2p
#
expcmd=""
expcmd=$(echo "$output" | grep Set-Cookie | sed -n 2p | awk -v FS="(Set-Cookie: |;)" '{print "export cookie=\"Cookie: " $2 "\""}')
http_return=""
http_return=$(echo "$output" | grep '< HTTP')
#echo "Login Status : " "$login_status"
# echo "New JSESSIONID EXPORT command: " "$expcmd"
if [ "$login_status" == "op.successfully" ]; then
echo "--------------------------------------------------------------------------------------------------------"
echo "HTTP Return Code: " "$http_return"
echo "Login OK : Javascript Return Status:" "$login_status"
echo "Run New JSESSIONID EXPORT command: \$" "$expcmd"
echo "--------------------------------------------------------------------------------------------------------"
elif [ "$login_status" == "op.verifyCode.fail" ]; then
echo "--------------------------------------------------------------------------------------------------------"
echo "HTTP Return Code: " "$http_return"
echo "Login Failded - Wrong verification Code : Javascript Return Status:" "$login_status"
echo "Login to WebSite and enter verification Code - after successfull login rerun this script !"
echo "--------------------------------------------------------------------------------------------------------"
else
echo "--------------------------------------------------------------------------------------------------------"
echo "HTTP Return Code: " "$http_return"
echo "Login failed check Login credentials - Javascript Return Status: " "$login_status"
echo "--------------------------------------------------------------------------------------------------------"
fi
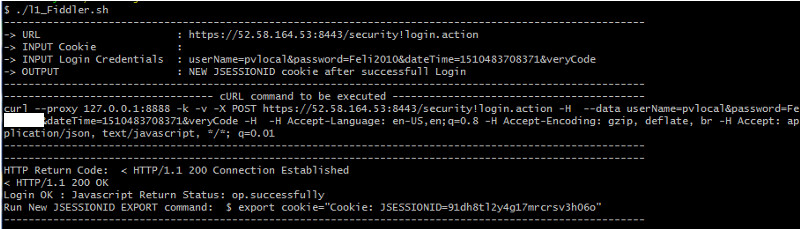
Testing the bash Script WRlogin.sh
$ ./WRlogin.sh
--------------------------------------------------------------------------------------------------------
-> URL : https://52.58.164.53:8443/security!login.action
-> INPUT Cookie : Cookie: JSESSIONID=17grbvbtwu2ga9blndj7rfrsk
-> INPUT Login Credentials : userName=pvlocal&password=Feli2010&dateTime=1510483708371&veryCode
-> OUTPUT : NEW JSESSIONID cookie after successfull Login
--------------------------------------------------------------------------------------------------------
---------------------------------- cURL command to be executed -----------------------------------------
curl -k -v https://52.58.164.53:8443/security!login.action -H Cookie: JSESSIONID=17grbvbtwu2ga9blndj7rfrsk --data userName=pvlocal&password=Feli2010&dateTime=1510483708371&veryCode -H X-CSRF-TOKEN: c3d70f5d-4388-4d85-a1db-9ac797b92418 -H Accept-Language: en-US,en;q=0.8 -H Accept-Encoding: gzip, deflate, br -H Accept: application/json, text/javascript, */*; q=0.01
--------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------
HTTP Return Code: < HTTP/1.1 200 OK
Login OK : Javascript Return Status: op.successfully
Run New JSESSIONID EXPORT command: $ export cookie="Cookie: JSESSIONID=rudqwfhaqx0m1mchkau9ycqzs"
--------------------------------------------------------------------------------------------------------
What we learned in Step 1
- A sucessful login returns message {"retMsg":"op.successfully"} and a new JSESSIONID
- This JSESSIONID need to be used for subsequent HTTP/AJAX request
- Note: At this stage we are able to attack this page using a brute FORCE methode
Step 2: Implement the Login Redirect using bash/cURL
- After as succesfull login the page is redirectet to securitys!tologin.action
- For the complete JS Code review Step 1
if (res.retMsg == "op.successfully") {
window.location.href = newPath + "securitys!tologin.action";
return;
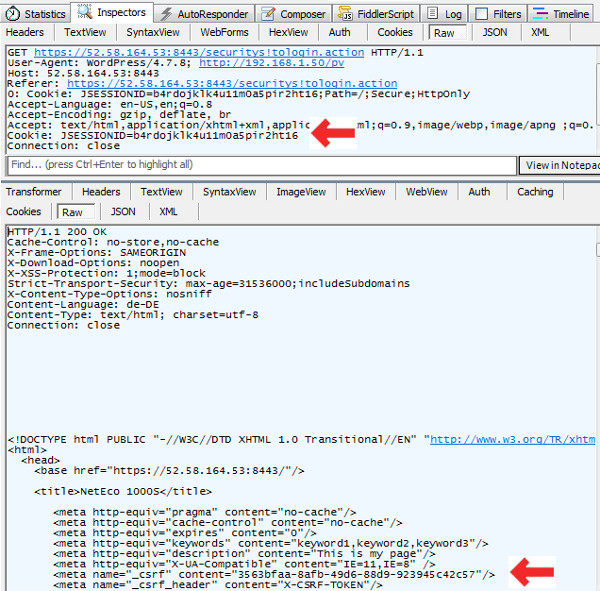
Use Google Dev tools to extract cURL bash Code
- Login to the WebSite
- Navigate to Network Tab
- Locate the securitys!tologin.action Request
- Select “Copy” -> “Copy as cURL (bash)”
| Initial page |
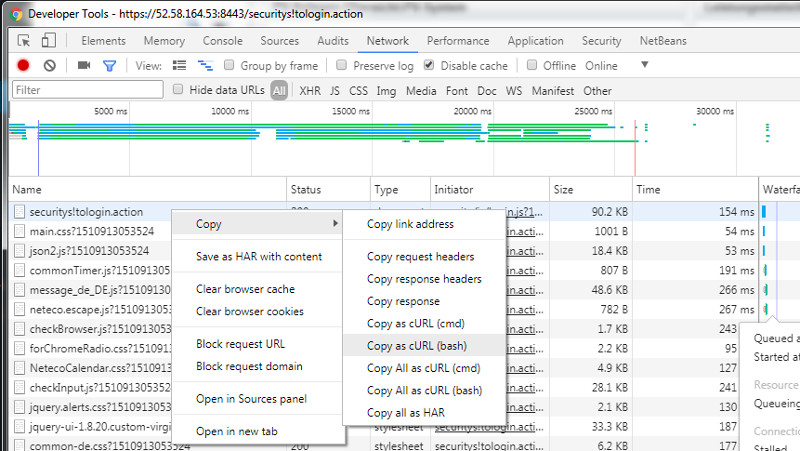 |
Paste the Code to a bash Shell
$ curl 'https://52.58.164.53:8443/securitys!tologin.action' -H 'Pragma: no-cache' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.9' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.94 Safari/537.36' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8' -H 'Referer: https://52.58.164.53:8443/index.action' -H 'Cookie: JSESSIONID=1b0miyons0sfl1uqxsbhdv0zud' -H 'Connection: keep-alive' -H 'Cache-Control: no-cache' --compressed --insecure
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
<br />
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"><br />
<html><br />
<head><br />
<base href="https://52.58.164.53:8443/"/><br />
<title>NetEco 1000S</title><br />
<meta http-equiv="pragma" content="no-cache"/><br />
<meta http-equiv="cache-control" content="no-cache"/><br />
<meta http-equiv="expires" content="0"/><br />
<meta http-equiv="keywords" content="keyword1,keyword2,keyword3"/><br />
<meta http-equiv="description" content="This is my page"/><br />
<meta http-equiv="X-UA-Compatible" content="IE=11,IE=8" /><br />
<meta name="_csrf" content="508a5c53-6d3d-4ed1-b56e-e292fcf0a2dc"/><br />
<meta name="_csrf_header" content="X-CSRF-TOKEN"/><br />
Keep special attention to _crsf HTML meta tags returned from above cURL request
- Note this CRSF Tojne will be used to access the Website !
meta name="_csrf" content="508a5c53-6d3d-4ed1-b56e-e292fcf0a2dc"
meta name="_csrf_header" content="X-CSRF-TOKEN"
Build script WRLogin2.sh to simulate the Page redirect
#!/bin/bash
#
# Use Googel Dev dev tools and select Copy as cURL (bash) to learn quickly about the Curl Syntax for a HTML request
#
# Use curl -i to get the response header dumped for this GET request
# This allows us to track the response cookies
# Usage :
# This script uses the new JSESSIONID returned from login.sh
# This script returns the csrf_token which can be finally used for all subseqent server connections
# export csrf_token="X-CSRF-TOKEN: 59bbc7b3-5c50-4220-b609-9506aaa83ea4"
#
url="https://52.58.164.53:8443/securitys!tologin.action"
echo "--------------------------------------------------------------------------------------------------------"
echo "-> URL :" $url
echo "-> INPUT Cookie JSESSIONID :" $cookie
echo "-> OUTPUT :" X-CSRF-TOKEN extract from HTML META _csrf
echo "--------------------------------------------------------------------------------------------------------"
# DebugON set, possibly to the empty string will printout add. trace info
# To enable Debugging run: $ export DebugON
#
if [ $DebugON ]; then
echo "DebugON is set, possibly to the empty string"
set -x
fi
#
# Only use the needed HTTP header Fields - Most Http Header Fields copied from our Google DEV Tool cURL copy we do not need
curl_header1='Accept-Language: en-US,en;q=0.8'
curl_header2='Accept-Encoding: gzip, deflate, br'
curl_header3='Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8'
#
# Arrays makes this much easier. Don't use Quotes here as $cookie and $csrf_token content uses spaces !
#
args=("-k" "-v" "$url" -H "$cookie" -H "$csrf_token" -H "$curl_header1" -H "${curl_header2}" -H "${curl_header3}")
#
echo "---------------------------------- cURL command to be executed -----------------------------------------"
echo "curl " "${args[@]}"
echo "--------------------------------------------------------------------------------------------------------"
#
# Execute Curl Command and save stdout and stderr to a Shell variable
output=$( curl "${args[@]}" 2>&1 )
#
# login2.sh retuns only a NEW X-CSRF-TOKEN via response META Tags _crsf
# We need to extract the crsf_token from the HTML repsonse Meta header and use if for furhter requests together with JSESSIONID !
#
#
#
# - Rerunning login2.sh may result that _crsf meta will be returne 2x.
# ->Just stop the awk script if we have found X-CSRF-TOKEN
# by callung exit.
# - Note we search for string _csrf" to limit the lines returned
#
csrf_token=""
csrf_token=$(echo "$output" | grep '_csrf\" content' | awk -v FS="(content=\"|\"/>)" '{print "export csrf_token=\"X-CSRF-TOKEN: " $2 "\""; exit }' )
http_return=""
http_return=$(echo "$output" | grep '< HTTP')
if [ -n "$csrf_token" ]; then
echo "--------------------------------------------------------------------------------------------------------"
echo "HTTP Return Code: " $http_return
echo " Note: Dont forget to set \$csrf_token variable extracted from HTML Meta Data ! "
echo " Run: \$" "$csrf_token"
echo "--------------------------------------------------------------------------------------------------------"
else
echo "--------------------------------------------------------------------------------------------------------"
echo "ERROR : X-CSRF-TOKEN not found !"
echo "HTTP Return Code: " $http_return
echo "--------------------------------------------------------------------------------------------------------"
fi
Test script WRLogin2.sh to simulate the Page redirect
- WRlogin2.sh extracts the X-CSRF-TOKEN from HTML Meta Tags
- Together with JSESSIONID return from WRLogin.sh this Info is used to access our target WEBSite
$ ./WRlogin2.sh
--------------------------------------------------------------------------------------------------------
-> URL : https://52.58.164.53:8443/securitys!tologin.action
-> INPUT Cookie JSESSIONID : Cookie: JSESSIONID=rudqwfhaqx0m1mchkau9ycqzs
-> OUTPUT : X-CSRF-TOKEN extract from HTML META _csrf
--------------------------------------------------------------------------------------------------------
---------------------------------- cURL command to be executed -----------------------------------------
curl -k -v https://52.58.164.53:8443/securitys!tologin.action -H Cookie: JSESSIONID=rudqwfhaqx0m1mchkau9ycqzs -H X-CSRF-TOKEN: c3d70f5d-4388-4d85-a1db-9ac797b92418 -H Accept-Language: en-US,en;q=0.8 -H Accept-Encoding: gzip, deflate, br -H Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
--------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------
HTTP Return Code: < HTTP/1.1 200 OK
Note: Dont forget to set $csrf_token variable extracted from HTML Meta Data !
Run: $ export csrf_token="X-CSRF-TOKEN: 218df123-fa18-44ba-8f3f-2dbc378e987c"
--------------------------------------------------------------------------------------------------------
Step 3: Finally Implement the Page Access using bash/cURL
- For this script we need: JSESSIONID returned from WRlogin.sh
- X-CSRF-TOKEN retuned from WRlogin2,sh
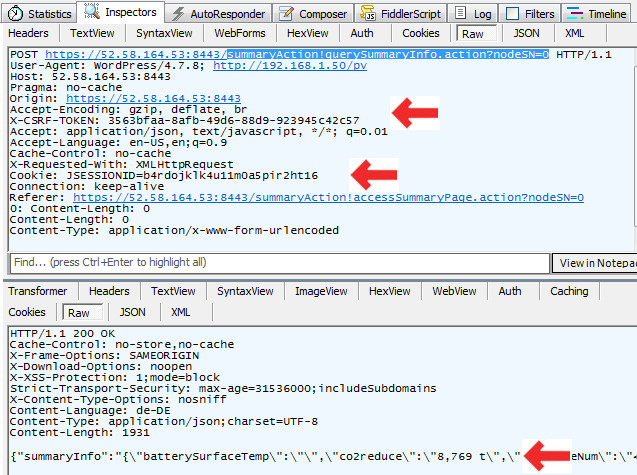
Follow the steps from above to extract the cURL bash command
$ curl 'https://52.58.164.53:8443/summaryAction!querySummaryInfo.action?nodeSN=0' -X POST -H 'Pragma: no-cache' -H 'Origin: https://52.58.164.53:8443' -H 'Accept-Encoding: gzip, deflate, br' -H 'X-CSRF-TOKEN: 508a5c53-6d3d-4ed1-b56e-e292fcf0a2dc' -H 'Accept-Language: en-US,en;q=0.9' -H 'User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.94 Safari/537.36' -H 'Accept: application/json, text/javascript, */*; q=0.01' -H 'Cache-Control: no-cache' -H 'X-Requested-With: XMLHttpRequest' -H 'Cookie: JSESSIONID=1b0miyons0sfl1uqxsbhdv0zud' -H 'Connection: keep-alive' -H 'Referer: https://52.58.164.53:8443/summaryAction!accessSummaryPage.action?nodeSN=0' -H 'Content-Length: 0' --compressed --insecure
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1932 100 1932 0 0 1932 0 0:00:01 --:--:-- 0:00:01 7263
...... -->Respone is JSON Encoded
"summaryInfo":"{\"batterySurfaceTemp\":\"\",\"co2reduce\":\"8,062 t\",\"converseNum\":\ ":\"EUR\",
\"currentPower\":\"3,860 kW\",\"dayPower\":\"12,170 kWh\",\"daytotalRadiation\":\"\",\"gridStatus\":false
.....
Build a bash shell script WRData.sh for simulating the WebSite Access
#!/bin/bash
#
# Use Google Dev dev tools and select Copy as cURL (bash) to learn quickly about the Curl Syntax for a HTML request
#
# Note to run this script we need a valid Env - The related export commands should be run after script executipn
#
# - JSESSIONID cookie -> login.sh -> export cookie="Cookie: JSESSIONID=18knsdija6tyjjmej043tac8m"
# - X-CSRF-TOKEN -> login2.sh -> export csrf_token='X-CSRF-TOKEN: 1de4c25b-724a-4b96-a187-c72b134a5b9f'
#
# --> When now rerunning this SCRIPT both CSRF data and JSESSIONID should not change anymore !
url="https://52.58.164.53:8443/summaryAction%21querySummaryInfo.action?nodeSN=0"
echo "--------------------------------------------------------------------------------------------------------"
echo "-> URL :" $url
echo "-> INPUT Cookie JSESSIONID :" $cookie
echo "-> INPUT X-CSRF-TOKEN :" $csrf_token
echo "-> OUTPUT :" HTML Content
echo "--------------------------------------------------------------------------------------------------------"
# DebugON set, possibly to the empty string will printout add. trace info
if [ $DebugON ]; then
echo "DebugON is set, possibly to the empty string"
set -x
fi
#
# Only use the needed HTTP header Fields - Most Http Header Fields copied from our Google DEV Tool cURL copy we do not need
curl_header1='Accept-Language: en-US,en;q=0.8'
curl_header2='Accept-Encoding: gzip, deflate, br'
curl_header3='Accept: application/json, text/javascript, */*; q=0.01'
#
# Arrays makes this much easier. Don't use Quotes here as $cookie and $csrf_token content uses spaces !
#
args=("-k" "-v" "-X" "POST" "$url" -H "$cookie" -H "$csrf_token" -H "$curl_header1" -H "${curl_header2}" -H "${curl_header3}")
#
echo "---------------------------------- cURL command to be executed -----------------------------------------"
echo "curl " "${args[@]}"
echo "--------------------------------------------------------------------------------------------------------"
output=$( curl "${args[@]}" 2>&1 )
#
#set +x
#
# String operation on Output
# awk -v FS="(currentPower|dayPower)" '{print $2 }' -> \":\"20,397 kW\",\"
# sed 's/...$//' --> removes the 3 last character [ including the 2.nd Commma ] -> \":\"20,397 kW\"
# | tr -d '\\":' --> removes \": from the remaing string : -> 20,397 kW
#
# Note : Don't use kW or kWh as FS for the awk command as this may break awk due to multiple occurance of these strings
# in the HTMT reponse !
#
current_power=""
current_power=$(echo "$output" | grep 'summaryInfo' | awk -v FS="(currentPower|dayPower)" '{print $2 }' | sed 's/...$//' | tr -d '\\":' )
day_power=""
day_power=$(echo "$output" | grep 'summaryInfo' | awk -v FS="(dayPower|daytotalRadiation)" '{print $2 }' | sed 's/...$//' | tr -d '\\":' )
http_return=""
http_return=$(echo "$output" | grep '< HTTP')
echo "--------------------------------------------------------------------------------------------------------"
date
echo "HTTP Return Code: " $http_return
echo "Current Power : " $current_power
echo " Day Power : " $day_power
echo "--------------------------------------------------------------------------------------------------------"
Test bash shell script WRData.sh to access our target WebSite
$ ./WRData.sh
--------------------------------------------------------------------------------------------------------
-> URL : https://52.58.164.53:8443/summaryAction%21querySummaryInfo.action?nodeSN=0
-> INPUT Cookie JSESSIONID : Cookie: JSESSIONID=rudqwfhaqx0m1mchkau9ycqzs
-> INPUT X-CSRF-TOKEN : X-CSRF-TOKEN: 218df123-fa18-44ba-8f3f-2dbc378e987c
-> OUTPUT : HTML Content
--------------------------------------------------------------------------------------------------------
---------------------------------- cURL command to be executed -----------------------------------------
curl -k -v -X POST https://52.58.164.53:8443/summaryAction%21querySummaryInfo.action?nodeSN=0 -H Cookie: JSESSIONID=rudqwfhaqx0m1mchkau9ycqzs -H X-CSRF-TOKEN: 218df123-fa18-44ba-8f3f-2dbc378e987c -H Accept-Language: en-US,en;q=0.8 -H Accept-Encoding: gzip, deflate, br -H Accept: application/json, text/javascript, */*; q=0.01
--------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------
Fr, 17. Nov 2017 10:09:24
HTTP Return Code: < HTTP/1.1 200 OK
Current Power : 3,846 kW
Day Power : 3,770 kWh
--------------------------------------------------------------------------------------------------------
Final test of our developed Shell Scripts
$ ./WRlogin.sh
--------------------------------------------------------------------------------------------------------
-> URL : https://52.58.164.53:8443/security!login.action
-> INPUT Cookie : Cookie: JSESSIONID=rudqwfhaqx0m1mchkau9ycqzs
-> INPUT Login Credentials : userName=pvlocal&password=Feli2010&dateTime=1510483708371&veryCode
-> OUTPUT : NEW JSESSIONID cookie after successfull Login
--------------------------------------------------------------------------------------------------------
---------------------------------- cURL command to be executed -----------------------------------------
curl -k -v https://52.58.164.53:8443/security!login.action -H Cookie: JSESSIONID=rudqwfhaqx0m1mchkau9ycqzs --data userName=pvlocal&password=Feli2010&dateTime=1510483708371&veryCode -H -H Accept-Language: en-US,en;q=0.8 -H Accept-Encoding: gzip, deflate, br -H Accept: application/json, text/javascript, */*; q=0.01
--------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------
HTTP Return Code: < HTTP/1.1 200 OK
Login OK : Javascript Return Status: op.successfully
Run New JSESSIONID EXPORT command: $ export cookie="Cookie: JSESSIONID=slz60pg4qbqp1bxj6gcrfhgdw"
--------------------------------------------------------------------------------------------------------
$ export cookie="Cookie: JSESSIONID=slz60pg4qbqp1bxj6gcrfhgdw"
$ ./WRlogin2.sh
--------------------------------------------------------------------------------------------------------
-> URL : https://52.58.164.53:8443/securitys!tologin.action
-> INPUT Cookie JSESSIONID : Cookie: JSESSIONID=slz60pg4qbqp1bxj6gcrfhgdw
-> OUTPUT : X-CSRF-TOKEN extract from HTML META _csrf
--------------------------------------------------------------------------------------------------------
---------------------------------- cURL command to be executed -----------------------------------------
curl -k -v https://52.58.164.53:8443/securitys!tologin.action -H Cookie: JSESSIONID=slz60pg4qbqp1bxj6gcrfhgdw -H -H Accept-Language: en-US,en;q=0.8 -H Accept-Encoding: gzip, deflate, br -H Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
--------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------
HTTP Return Code: < HTTP/1.1 200 OK
Note: Dont forget to set $csrf_token variable extracted from HTML Meta Data !
Run: $ export csrf_token="X-CSRF-TOKEN: 3fa4555c-0890-4806-a7f1-ad0ffcf6fa41"
--------------------------------------------------------------------------------------------------------
$ export csrf_token="X-CSRF-TOKEN: 3fa4555c-0890-4806-a7f1-ad0ffcf6fa41"
$ ./WRData.sh
--------------------------------------------------------------------------------------------------------
-> URL : https://52.58.164.53:8443/summaryAction%21querySummaryInfo.action?nodeSN=0
-> INPUT Cookie JSESSIONID : Cookie: JSESSIONID=slz60pg4qbqp1bxj6gcrfhgdw
-> INPUT X-CSRF-TOKEN : X-CSRF-TOKEN: 3fa4555c-0890-4806-a7f1-ad0ffcf6fa41
-> OUTPUT : HTML Content
--------------------------------------------------------------------------------------------------------
---------------------------------- cURL command to be executed -----------------------------------------
curl -k -v -X POST https://52.58.164.53:8443/summaryAction%21querySummaryInfo.action?nodeSN=0 -H Cookie: JSESSIONID=slz60pg4qbqp1bxj6gcrfhgdw -H X-CSRF-TOKEN: 3fa4555c-0890-4806-a7f1-ad0ffcf6fa41 -H Accept-Language: en-US,en;q=0.8 -H Accept-Encoding: gzip, deflate, br -H Accept: application/json, text/javascript, */*; q=0.01
--------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------
Fr, 17. Nov 2017 12:24:10
HTTP Return Code: < HTTP/1.1 200 OK
Current Power : 3,949 kW
Day Power : 13,890 kWh
--------------------------------------------------------------------------------------------------------
$ ./WRData.sh
--------------------------------------------------------------------------------------------------------
-> URL : https://52.58.164.53:8443/summaryAction%21querySummaryInfo.action?nodeSN=0
-> INPUT Cookie JSESSIONID : Cookie: JSESSIONID=slz60pg4qbqp1bxj6gcrfhgdw
-> INPUT X-CSRF-TOKEN : X-CSRF-TOKEN: 3fa4555c-0890-4806-a7f1-ad0ffcf6fa41
-> OUTPUT : HTML Content
--------------------------------------------------------------------------------------------------------
---------------------------------- cURL command to be executed -----------------------------------------
curl -k -v -X POST https://52.58.164.53:8443/summaryAction%21querySummaryInfo.action?nodeSN=0 -H Cookie: JSESSIONID=slz60pg4qbqp1bxj6gcrfhgdw -H X-CSRF-TOKEN: 3fa4555c-0890-4806-a7f1-ad0ffcf6fa41 -H Accept-Language: en-US,en;q=0.8 -H Accept-Encoding: gzip, deflate, br -H Accept: application/json, text/javascript, */*; q=0.01
--------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------
Fr, 17. Nov 2017 12:24:16
HTTP Return Code: < HTTP/1.1 200 OK
Current Power : 3,949 kW
Day Power : 13,890 kWh
--------------------------------------------------------------------------------------------------------
Reference
DVWA - Main Login Page - Brute Force HTTP POST Form With CSRF Token